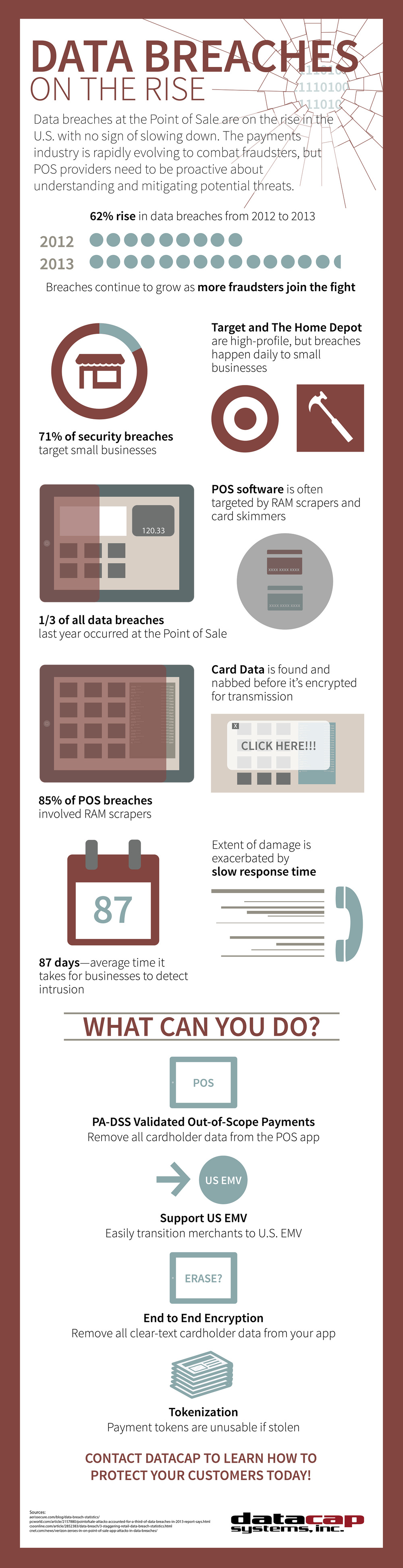
![]()
The EMV liability shift has been a reality of the retail marketplace since it went into effect on Oct. 1, 2015. As more and more chip cards are issued and more merchants begin to update their point of sale to enable support for EMV, merchants will begin to see the positive results of the change. The EMV liability shift was implemented in the name of security and the protection of customer data, and while EMV certainly protects against card-present fraud, it alone is not enough to protect against hackers and other cybercriminals who are targeting card data in-transit.
From a merchant’s perspective, point to point encryption and tokenization should be prioritized ahead of EMV – or at least included as essential pieces of the upgrade to an EMV-enabled payments solution. Because of the significantly higher risk/liability associated with site-wide data breaches, protecting card data in transit should be a merchant’s main focus. Whereas the merchant may be liable for the amount of a fraudulent transaction should they not move to an EMV-enabled solution, card data that’s compromised in a site-wide data-breach often results in hundreds of thousands in fines – likely a business-ender for most SMBs. EMV is small potatoes compared to the risk merchants are facing today if they’re not protecting their data in transit.

EMV
An up to date Point of Sale should have a plan in place for US EMV support. The technology exists to verify that a card is not a clone or other fraudulent form of payment. It also protects against skimming and other types of data theft at the point of sale by generating a random, transaction specific code that cannot be used to create a copy of the card in the future. While EMV does a good job of protecting a customer’s card, it does nothing to protect a retailer’s internal system, which is where most of the biggest data breaches have originated.
Point-to-point encryption
The next layer needed in a robust security environment is point-to-point encryption. P2PE is a process that encrypts card data at the moment it interacts with the point of sale terminal and keeps it secure all the way through a merchants system, Jeremy King, international director at PCI Security Standards Council told Essential Retail. This type of encryption can defend against point of sale malware attacks that hijack card data from within a merchants system after the initial swipe or tap. The encryption ensures that the card data is unbreachable at every step of a merchant’s payments process. Many of the highest profile retail data breaches like the Target breach in 2013 were the result of point of sale malware – P2PE addresses these type of attacks.
Tokenization
The third layer of security needed to keep customer data as secure as possible is tokenization. This step defends any data that’s being stored inside a retailers system for later use. As explained by Network World, sensitive data like a credit card or social security number is placed into an encrypted folder known as a vault and replaced with a random string of characters called a token on the retailers system. When the data is needed later, the system compares that token with the vault, which is heavily encrypted. Once found, the true value can be used in place of the token in order to complete the transaction. This layer of security keeps stored customer data safe and separated from the POS – a hacker who gained access to a merchant’s system would only get the tokens, which are useless without the library to look up the true values.
Though the EMV liability shift has, and will continue help retailers protect their customers, it is not enough by itself to protect customer and merchant data. In order to be truly secure, merchants should look at EMV cards as simply the first step on the road to complete security. By using EMV along with encryption and tokenization, a retailer can be sure that their system is protected against fraudsters.